Manage OT and IIoT Machine Identities
IT-SA 2025 | October 07 - 09 | Hall 7, booth 421
We Show Innovative Solutions to automate certificate lifecycle in IoT.
Visit Us at IT-SA
For Free
Through our Siemens partnership, you can claim your free ticket now.
Don’t miss the chance to connect with our experts and explore the latest in PKI & OT security.
Visit our Siemens partner to ensure you a free visit ITSA!
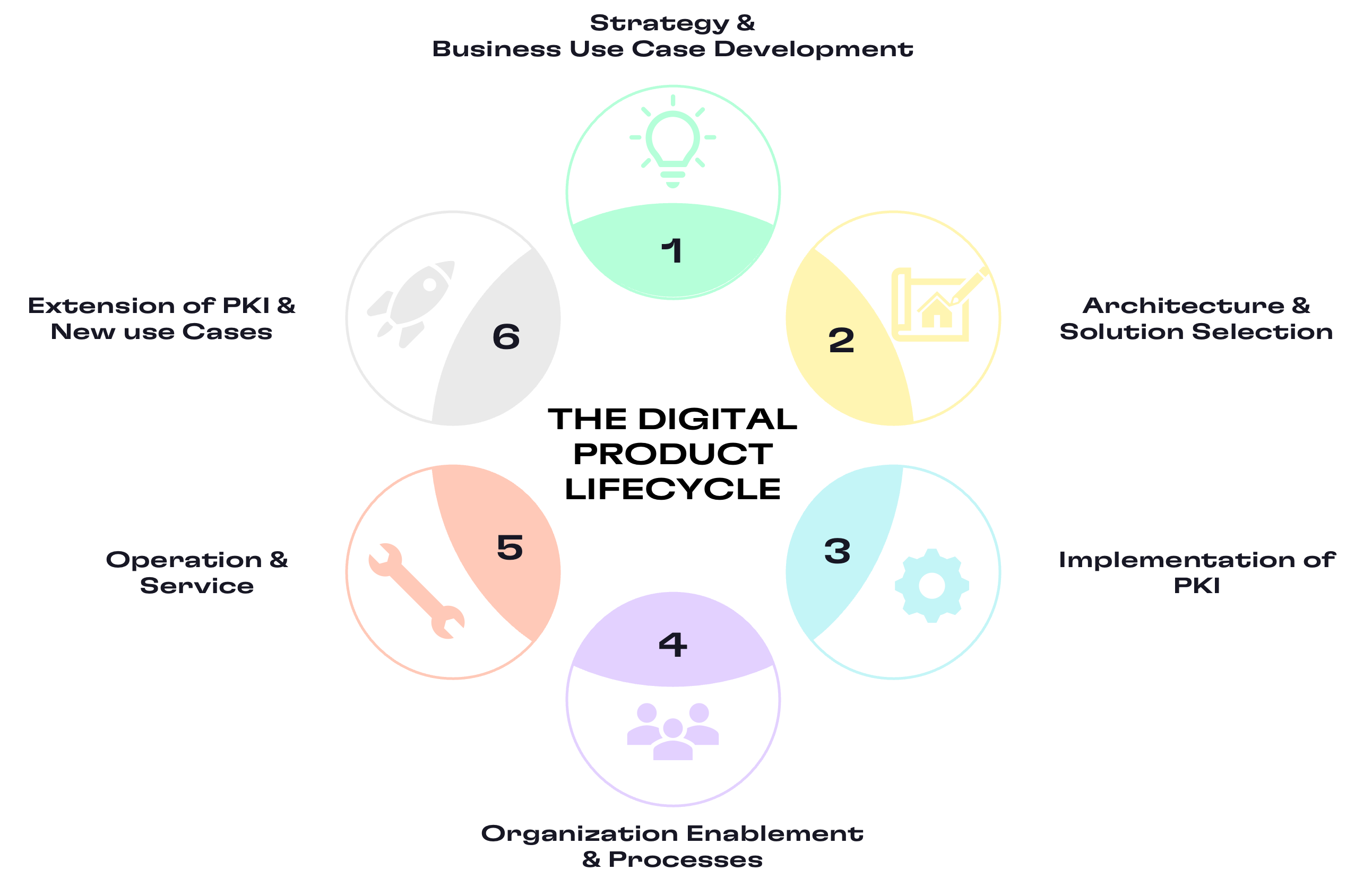
we will Bring use cases all along the digital product lifecycle
01
Strategy
Your challenges: Managing digital identities, meeting strict regulations, and building a scalable PKI strategy often feel overwhelming and unclear.
Our solution: We guide you in defining business-driven PKI use cases and developing a secure, compliant, and future-proof identity environment.
02
Architecture
Your challenges: Designing the right PKI architecture means tough choices — hierarchy, enrollment protocols, endpoint management, and on-prem vs. managed — with high stakes and no room for mistakes.
Our solution:We deliver clarity and precision in PKI design — from hierarchy and protocols to endpoint management — enabling fast, secure, and sustainable rollout.
03
Implementation
Your challenges: PKI rollout isn’t just “install and run” — it’s complex testing, secure key management, and constant updates that consume skilled resources you can’t spare.
Our solution: We take over the heavy lifting of PKI implementation — from automation and upgrades to certificate validation — cutting your workload and freeing your experts to focus on what drives the business.
04
Processes
Your challenges: PKI success fails without clear ownership — fragmented teams, missing skills, undefined lifecycle processes, and endless documentation slow down security and create risk.
Our solution: We establish the right processes, roles, and documentation to enable your organization for PKI — cutting through chaos and freeing your teams to run securely and efficiently.
05
Operations
Your challenges: Running PKI operations drains resources — constant updates, monitoring, troubleshooting, and revocation management turn into a never-ending cycle of fire-fighting.
Our solution: We operate and optimize your PKI end-to-end, ensuring stability, compliance, and continuous improvement — so your teams can stop firefighting and focus on innovation.
06
Extension
Your challenges: Business growth and new requirements force PKI to evolve — new use cases, automation needs, and documentation updates that strain your teams and risk gaps.
Our solution: We extend and adapt your PKI seamlessly, integrating new use cases and automation improvements while keeping processes, components, and documentation fully aligned.
How to build your Public Key Infrastructure Environement

Our Solutions for your producitivity
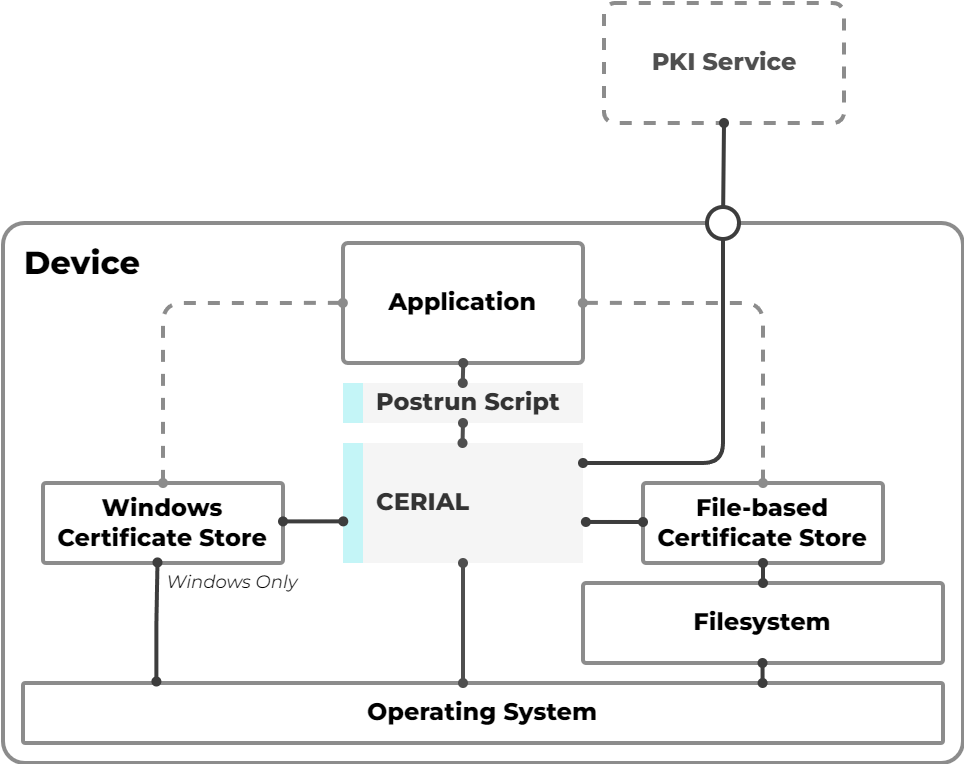
CERIAL
With our CERIAL solution, you automate your certificate lifecycle management on your IT Assets with ease! Whether the IT Assets are in your IT Infrastructure or within your OT Network, CERIAL automates the request and renewal of certificates for various use cases and frees you up for important work.

OT CONNECTOR
Manage your OPC UA certificates with our OT Connector, which implements GDS Push for a Zero Footprint certificate lifecycle automation on process components.
Our solution integrates with REST-based repositories, such as CMDBs or other asset inventories and allows to detect changes on assets, which require the enrollment of new certificates or execute change on existing certificates.
A strong team for you

&

Learn to integrate pKI with Ease into your value chain

Certificate Automation with GDS Push
Our demo setup includes use cases, where we will show you the automatic management of OPC UA server certificates. BxC Security as certified cybersecurity partner of Siemens and Nexus have exclusive demo setups, where we show you the ease of certificate automation in OPC UA environments. Without significant certificate automation, PKI will never be able to support OT environments to a considerable extent. We show you how you achieve that with ease!

Certificate Automation For IT and IIoT Devices
We are going to bring our award-winning CERIAL solution to show you how easy the integration of certificate lifecycle management into your Windows, Linux and ARM-based systems can be! No central control plane for certificate orchestration, your system operators decide about the individual need for every instance. This allows you to keep full control of your assets' behavior and frees you up from certificate enrollment and renewal tasks. We show you how easy CERIAL is being deployed and running in a minute!

Secure device iDs at scale
You are an IoT or IIoT component or device manufacturer? Then do not miss the opportunity to see how easy and flexible secure identities can be created and deployed to your assets. Whether you produce in-house or have suppliers for this task, we have the right solution for you to get secure and reliable asset identities from the very beginning of the production process.
Master regulatory requirements and provide your customers with modern and secure products! With secure identities, your customers will benefit from modern lifecycle processes to integrate and manage your products at scale.

product integrity with ease
Whether you are a component or device vendor and provide products to your customers or you are an operator who aims at automating your operational processes. Integrity of code is the most powerful security measure to prevent malicious functions are executed in your environment!
We show you how you can integrate code signing processes into your operations and product lifecycle by easy integration with Nexus Signing Authority! No matter if you want to integrate your firmware for being signed or have in mind to manage your Powershell scripts with digital signatures to ensure resilience in your production IT - we show you how.
